the cyber resilience capability maturity model (CR-CMM) lets you measure, benchmark, and improve resilience across ten domains.
The Cyber Resilience Capability Maturity Model (CR-CMM), inspired by the SOC-CMM and CTI-CMM, will focus on the maturity and effectiveness of an organization's ability to withstand, recover from, and adapt to cyber threats, leveraging the insights from NIST 800-160 and MITRE frameworks.
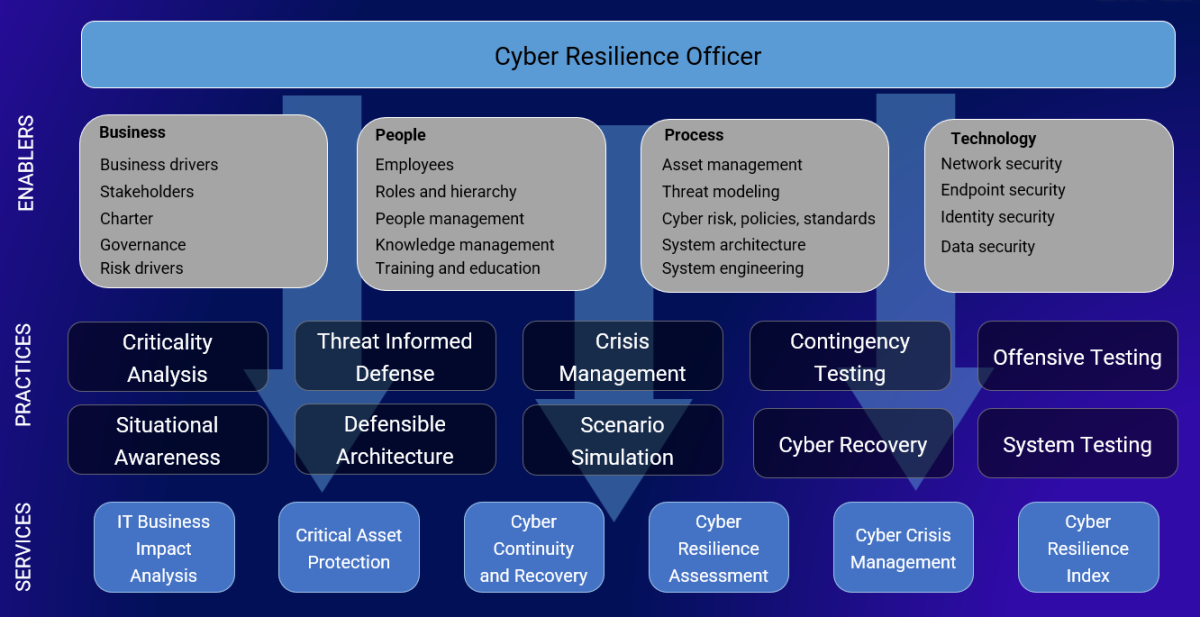
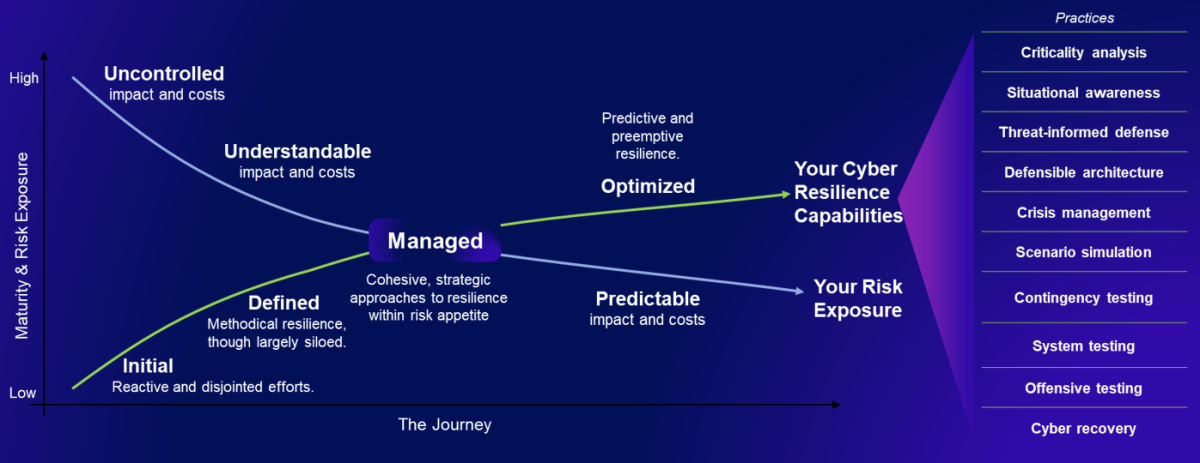
The model will be structured around key domains that mirror those used in the SOC-CMM, such as Technology, Process, People, and Business, but adapted to emphasize cyber resilience Services. There are ten core Practices that are leveraged to build capabilities, which are visible in the slide below. These sit at the heart of the CR-CMM.
The maturity levels range from Initial (where resilience practices are reactive and uncoordinated) to Optimized (where resilience is proactive, integrated into all aspects of system design, and supported by continuous improvement).
The CR-CMM will be highly customizable by organizations, enabling them to tailor it to specific threat environments and operational contexts, similar to how NIST SP 800-160 allows for flexibility in applying its resilience constructs based on organizational risk tolerance and system complexity.
The first open standard for cyber resilience maturity. Built by practitioners, for practitioners.
“With a one-hour workshop we pinpointed our biggest resilience gaps and secured budget the same week.”
CISO, healthcare sector

faq - the CR-CMM filters the signal from the noise
1. What strategic problem does CR-CMM solve?
Boards need proof the organization can actually survive cyber disruption, not just pass audits and comply with rules. CR-CMM concretely measures with precision an organization’s real-life ability to anticipate, withstand, recover and adapt, then converts the results into an actionable, costed roadmap that executives can approve and operational teams can execute.
Boards need proof the organization can actually survive cyber disruption, not just pass audits and comply with rules. CR-CMM concretely measures with precision an organization’s real-life ability to anticipate, withstand, recover and adapt, then converts the results into an actionable, costed roadmap that executives can approve and operational teams can execute.
2. Why introduce CR-CMM when NIST CSF 2.0, ISO 27001, ISO 22301 and similar frameworks already exist?
Existing frameworks like NIST CSF describe what good looks like but leave gaps in the cyber-to-business resilience and continuity intersection. CR-CMM is not another framework. It consolidates that spectrum by leveraging world-class best practice and shows how to achieve cyber resilience: 151 evidence-based checkpoints, maturity scoring and an automated prioritization engine built on industry best practice and regulatory requirements. Leaders get turn-by-turn guidance, not just a compass.
Existing frameworks like NIST CSF describe what good looks like but leave gaps in the cyber-to-business resilience and continuity intersection. CR-CMM is not another framework. It consolidates that spectrum by leveraging world-class best practice and shows how to achieve cyber resilience: 151 evidence-based checkpoints, maturity scoring and an automated prioritization engine built on industry best practice and regulatory requirements. Leaders get turn-by-turn guidance, not just a compass.
3. What validates the model’s credibility?
CR-CMM combines CMMI measurement discipline with control mappings from NIST 800-160, NIST 800-172, MITRE ATT&CK and ISO 27001. Developed by High Value Target with input from ISSA and the global Cyber Resilience Officer community, it is progressing through formal endorsements. Every question includes an evidence tag for audit transparency and risk control design traceability.
CR-CMM combines CMMI measurement discipline with control mappings from NIST 800-160, NIST 800-172, MITRE ATT&CK and ISO 27001. Developed by High Value Target with input from ISSA and the global Cyber Resilience Officer community, it is progressing through formal endorsements. Every question includes an evidence tag for audit transparency and risk control design traceability.
4. Will using CR-CMM add compliance workload?
No. Practical and material capability uplift is the goal; compliance mapping is embedded. Dashboards cross-reference major regulations (for example DORA and NIS2), eliminating duplicate data calls while still satisfying regulators.
No. Practical and material capability uplift is the goal; compliance mapping is embedded. Dashboards cross-reference major regulations (for example DORA and NIS2), eliminating duplicate data calls while still satisfying regulators.
5. What effort is required to run the assessment?
One half-day, facilitator-led workshop completes the initial self-assessment. The spreadsheet automates scoring and visualization. Reassess twice per year to track progress. Resource demand is measured in hours, not weeks. -
One half-day, facilitator-led workshop completes the initial self-assessment. The spreadsheet automates scoring and visualization. Reassess twice per year to track progress. Resource demand is measured in hours, not weeks. -
6. What tangible value does the company receive?
• Heat-mapped maturity profile that highlights weak links for immediate action.
• Ranked backlog with effort-and-impact scores for capital planning.
• Independent benchmarks as community adoption grows.Progress towards cyber resilience accountability and a clear operating model.
• Heat-mapped maturity profile that highlights weak links for immediate action.
• Ranked backlog with effort-and-impact scores for capital planning.
• Independent benchmarks as community adoption grows.Progress towards cyber resilience accountability and a clear operating model.
7. What are the licensing terms and cost model?
CR-CMM is released under Creative Commons Attribution-NonCommercial 4.0. Internal use is free. Commercial resale or derivative work requires written consent from the authors at High Value Target, protecting community benefit and intellectual property.
CR-CMM is released under Creative Commons Attribution-NonCommercial 4.0. Internal use is free. Commercial resale or derivative work requires written consent from the authors at High Value Target, protecting community benefit and intellectual property.
8. What if we have questions or need support executing the assessment?
The High Value Target team provides on-demand assistance and structured engagements for rapid or in-depth assessments. Consulting firms can benefit as well for trainings to either assess maturity or build cyber resilience operating models. Contact them at contact@highvaluetarget.com
The High Value Target team provides on-demand assistance and structured engagements for rapid or in-depth assessments. Consulting firms can benefit as well for trainings to either assess maturity or build cyber resilience operating models. Contact them at contact@highvaluetarget.com

